FBI Warns of Hackers Targeting US Infrastructure

Summary The FBI announced this week that there is likely going to be an increase in cyber-attacks against critical infrastructure by state-backed APTs (Advanced Persistent Threats). This includes utilities, oil pipelines, and other critical industries key to economic functions in the United States. The particular campaign warned about recently has the underlying goal of undermining […]
Democratizing AI for Everyone: A Look at Microsoft’s New AI Builder for Power Platform

The world of Artificial Intelligence (AI) can often feel shrouded in complexity, reserved for data scientists and programmers. But what if there was a way to harness the power of AI without needing years of specialized training? Enter Microsoft’s AI Builder, a revolutionary new feature within the Microsoft Power Platform that empowers anyone to leverage AI in their workflows.
Enhancing Cyber Resilience in Healthcare: Strategies for Mitigating Ransomware Attacks

In recent years, the healthcare industry has increasingly become a prime target for cyberattacks, with ransomware incidents posing significant threats to patient data security and operational continuity. The recent cyberattacks on United Health’s Change Healthcare payment system serve as stark reminders of the vulnerabilities inherent in healthcare IT infrastructure. As highlighted in a recent article […]
Wired for Disaster: The Hidden Risks of Neglected Structured Cabling
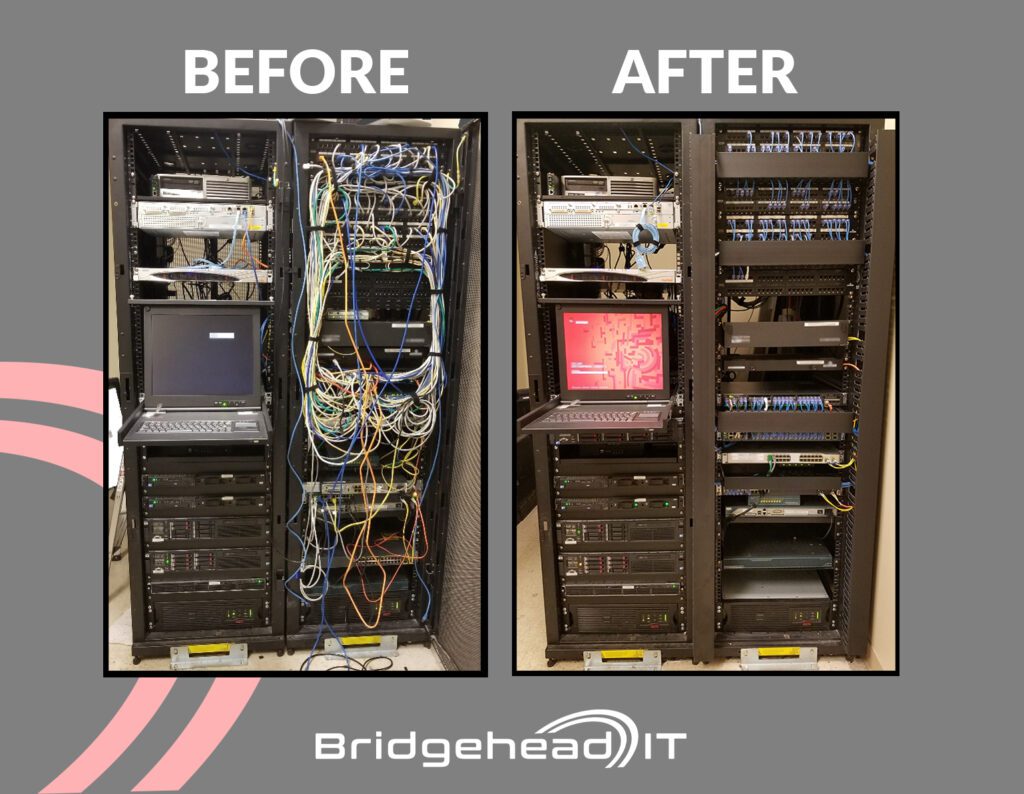
In the digital age, where seamless connectivity is vital, the importance of well-executed structured cabling services cannot be overstated. However, behind the scenes of every efficient network lies a potential disaster zone when cabling is neglected or improperly installed. In our latest exploration, we delve into the perils of subpar cabling practices and the detrimental […]
Recent Cyber Attacks on Healthcare Systems
The healthcare industry has been under fire recently, facing multiple cyber attacks that have crippled essential services and exposed sensitive patient data. These recent attacks underscore the growing threat that cybercrime poses to the healthcare industry. Over the past year numerous healthcare institutions have fallen victim to threat actors. The increasing nature of these attacks […]
Driving Success: The Crucial Role of Reporting in the Automotive Industry
In the fast-paced world of automotive retail, success isn’t just about selling cars; it’s about understanding the intricacies of your operations, analyzing performance metrics, and making informed decisions. This is where reporting steps in as a vital tool for dealerships, offering invaluable insights into various aspects of their business. From tracking sales performance to assessing […]
Bridgehead IT: Navigating the AI Revolution in Manufacturing

The winds of change are sweeping through the manufacturing industry. Automation,efficiency, and innovation are no longer optional add-ons, but the very lifeblood ofsurvival in a fiercely competitive global market. Enter Artificial Intelligence (AI), atransformative force poised to reshape not just how products are made, but how wework as well. Bridgehead IT is your trusted guide […]
Strategies for Eliminating Technical Debt

For business decision-makers, technology is no longer just a support system; it’s the engine driving growth and innovation. But this engine can sputter and cough if you ignore a hidden enemy: technical debt. Think of technical debt as shortcuts, workarounds, and temporary fixes accumulated over time. They might seem harmless initially, but left unchecked, they […]
Major Telecom Outage Highlights

Bridgehead IT: Your Trusted Partner for Secure and Efficient Development Imagine launching a brand-new app or deploying a critical software patch, only to have it crash for everyone. This recent scenario underscores the importance of robust development practices. “The outage, attributed to a coding error, highlights the need for better practices in software development and […]
Streamlined Products, Simplified Subscriptions

There’s been a shift in the VMware ecosystem. Broadcom’s recent overhaul of their product lineup and licensing model promises a simpler, more cost-effective approach for businesses. But navigating the changes can be daunting. This blog post cuts through the confusion, highlighting the key transformations and empowering you to make informed decisions for your organization. Two […]